Organise and Manage AWS Parameter Store
Contents
AWS Parameter Store is the part of AWS Systems Manager. It provides secure storage for parameters and secrets. And grant resilient availability. Let’s dive into it and see how to use it for micro-service platform.
Parameters organisation
For convenience and flexibility, we split parameters into the following categories:
- Platform parameters - generic for the whole system and all services;
- Service parameters - parameters specifc for dedicated service, can override platform parameters;
Following diagram describes how to organize parameters in microservice platform from generic to specific.
Platform environments
Before promoting the application to production normally it passes acceptance and automated tests. And for each stage services might use different databases and other resources. Therefore we store each parameter for different environments:
- Staging - environment for accepntance tests
- Testing - for integration tests
- Production
Parameter name convention
Names are important and convention help to keep them in a meaningful order. Following convention allows to store platform-specific parameter per environment:
| |
For example:
- /platform-name/platform-settings/account/feature-flag-1
- /platform-name/platform-settings/production/feature-flag-1
And the service-specific parameter has the following name convention:
| |
For example:
- /platform-name/account/staging/db-passw
- /platform-name/account/production/db-passw
Role policy configuration
Guided by best practices of just enough administration we should give a minimum amount of right for specific IAM role. Following AWS IAM policy grants developer access to staging environment only:
| |
For task runner role, such as AWS Lambda, ECS Task and so on policy need to limited to read-only for staging and production environments:
| |
Parameter Store UI
The easiest way to start an experiment with managing parameter store is open user interface: Services → System Manager → Parameter Store → Create parameter
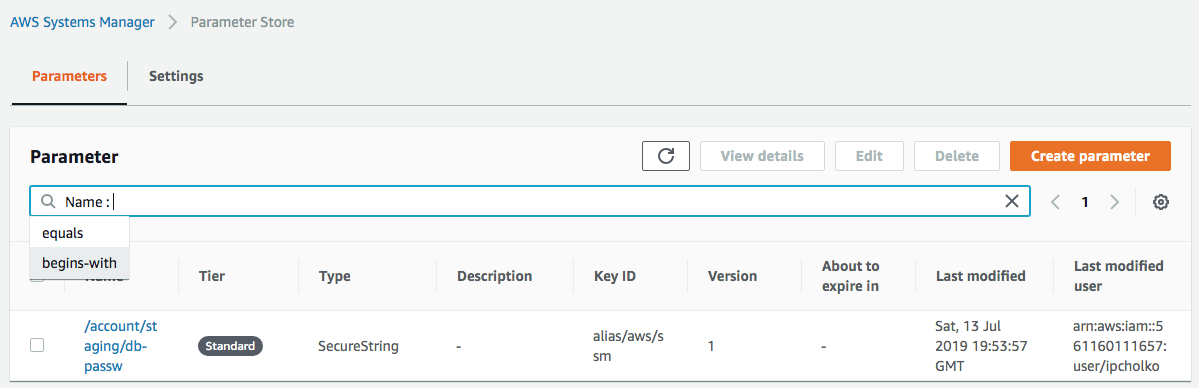
Let’s add new parameter:
| Name | /platform-name/account/staging/db-passw |
| Tier | Standard |
| Type | SecureString |
| KMS Key ID | alias/aws/ssm (default) |
| Value | passw |
Then you would see something like this in the screen:
This UI has quite limited functionality. However, AWS has a very powerful command-line toolchain to manage parameter store. Before dive into the CLI let’s take a look required policies.
Parameter Store CLI
Out of the box, AWS propose system manager command-line interface to manage the parameter store.
Let’s take a look at how to read the stored parameter:
| |
| |
Full list of commands can be found here: https://docs.aws.amazon.com/cli/latest/reference/ssm/index.html
- delete-parameter
- delete-parameters
- describe-parameters
- get-parameter
- get-parameter-history
- get-parameters
- get-parameters-by-path
- label-parameter-version
- put-parameter
Chamber CLI
Chamber is an alternative way of how to manipulate the parameter store.
It allows to import and export multiple parameters in json format.
Details can be found here: https://github.com/segmentio/chamber
Install
For OSX users you can use brew to install it:
| |
Setup environment to let chamber know what KMS key use for decrypt. You can add this to your shell profile file as well:
| |
Write
Let’s add more params to the parameter store. You could use json to specify the list of parameters:
| |
An alternative way is using STDIN to pass parameters in json:
| |
There are some limitations in json format:
- Key names can not contain
/symbols in the name. - Values can not be empty or null.
Read
Then let’s read what we stored in the parameter store. If you don’t have jq you can use brew install jq:
| |
| |
If you need to dump multiple parameters you can combine them in one export command:
| |
Delete
To delete key you can use:
| |
Afterword
AWS parameter store is comprehensive and non-expensive secret storage. Can be hardened via AWS lambda functions to achieve such feature as key rotations. This service recommended as secrets manager for any micro-service platform size.